Ransomware is a serious threat that locks down your device. Ransomware blocks you from accessing your data until you pay your attacker.
Microsoft Windows has a built-in service to protect your computer(s) from Ransomware attacks. Unfortunately, this critical security feature in Windows comes disabled by default. As a result, you need to turn this feature on NOW!
Table of Contents
Why You Need Ransomware Protection

The U.S. Department of Homeland Security continually issues CISA advisories for RansomWare attacks. One advisory comes in response to a cyberattack targeting an unnamed natural gas compression facility that employed spear-phishing to deliver ransomware to the company’s internal network, encrypting critical data and knocking servers out of operation for almost two days.
How Ransomware Can Attack
“A cyber threat actor used a spear-phishing link to obtain initial access to the organization’s information technology network before pivoting to its operational technology network. The threat actor then deployed commodity ransomware to encrypt data for impact on both networks,” CISA stated.
It is a clear indication that phishing attacks continue to be an effective means to bypass security barriers and that hackers don’t always need to exploit security vulnerabilities to breach organizations.
Hackers will first infiltrate the network and then prepare to hit the organization as a whole rather than 1 computer at a time, therefore causing the worst-case scenario and strongest impact on the target.
When Visser Precision (a Tesla part maker) was hit with ransomware, I wrote a post on LinkedIn to advise people to turn on Windows ransomware protection. I have had many inquiries on providing more details on how to protect Windows workstations from Ransomware.
Educational Institutes are Prime Targets
If you work in Education, you are especially vulnerable. In April of 2020, the education space experienced over 4.2 million malware infections, which makes up nearly 65 percent of the 6.5 million attacked devices, according to Microsoft.
How to Turn ON Ransomware Protection
Most people are unaware that a crucial security feature in Windows Defender comes disabled. By default the Ransomware Protection feature is off. Ransomware Protection was added to Windows in the October 2017 Windows 10 update.
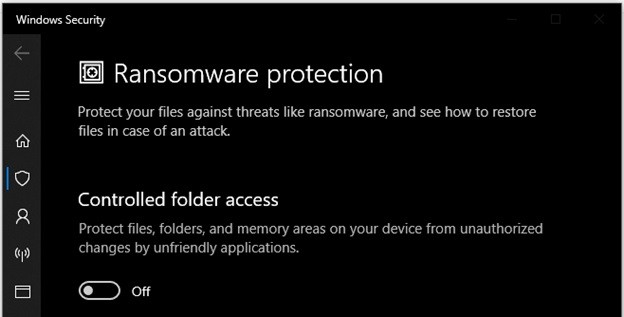
To turn this feature on, simply:
Identify Folders that contain your Data and Protect Them
- Open the Start Menu, then click the Settings icon.
- In the Settings menu, go to Update & Security > Windows Security > Virus & Threat Protection.
- Scroll down to Ransomware Protection and click “Manage Ransomware Protection.”
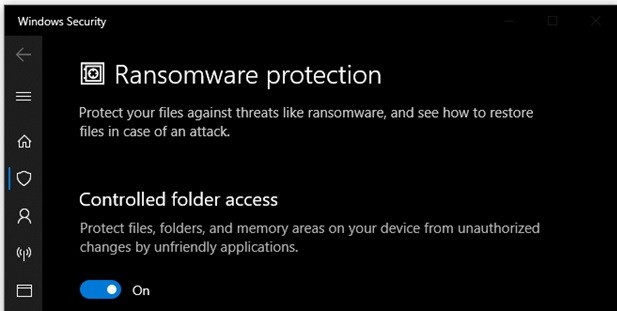
- In the next menu, enable “Controlled Folder Access.”
- Controlled Folder Access only protects certain folders by default: Documents, Pictures, Videos, Music, Desktop, Favorites. You can extend the Ransomware Protection to other files and folders by clicking “Add a protected folder” in that same window.
- Navigate to the folder you wish to add to the ransomware protection. Repeat for each folder you want to have protected.
Approve Applications to Access your Data
Now that you’ve set up Controlled Folder Access, Windows will monitor any programs that are accessing any files in the protected folders. Windows will block suspicious programs from trying to gain access. While this gives you some peace of mind, the problem is that not all “suspicious” programs are actually malicious. To avoid false positives, you can create a “whitelist” for Controlled Folder Access.
- Open the Start Menu and click the settings icon.
- Go to Update & Security > Windows Security > Virus & Threat Protection > Manage Ransomware Protection.
- Scroll down and click “Allow an app through controlled folder access,” then find and add the desired program to the list. You’ll have to repeat this process for each app you want to grant access to.
- You can also click “Block history” to view a list of programs that Windows Defender has prevented from accessing your protected files. Uninstall any programs you don’t recognize trying to access your files in controlled folders.
Anti-Ransomware Strategies
Ransomware goes after files stored in default locations like the Desktop and Documents folders. Ensure personal data areas (folders/directories) on your computer are included for “Controlled Folder Access”. Windows Defender antivirus tool foils ransomware attacks by denying unauthorized programs, services, or applications access to these locations. On any access attempt by an unknown program to a “controlled folder access” location, the user will be asked to allow access. If that notification comes out of the blue, not from anything you did yourself, block it!
Your #1 protection against Ransomware will always be Backups. Even with the ransomware protection from Windows Defender, you should also make sure you’re regularly backing up your files. This is so you don’t get locked out of anything important if ransomware strikes. Consider keeping your data backups in a secure, off-site location.

What to do if you encounter Ransomware
If you (or a client) encounter ransomware, you need to identify which version of ransomware you are dealing with.
Often, you will receive a ransom note that provides details about the type of ransomware your files have been encrypted with, but it can happen that you don’t have this information at hand.
ID Ransomware
The primary tool for identifying Ransomware is the ID Ransomware site.
Just a fantastic team put this site together. You start by uploading the ransom note, or a sample encrypted file. ID Ransomware will determine the type of ransomware and if your data can be unencrypted. You can also provide the contact addresses if no ransom note is available.
All too often after a ransomware attack, the first question is, “what encrypted my files?”, followed by “can I decrypt my data?”. This web service aims to help answer those questions, and guide a victim to the correct information relating to their infection.
By simply uploading a ransom note, and/or an encrypted file (preferably both for best results), the site will use several techniques to help identify what ransomware may have encrypted the files. This includes assessing the ransom note name, file name patterns of the encrypted file, and in some cases, even byte patterns in the encrypted file itself.
There are cases where multiple ransomware could be detected, as some ransomware share signs. It is also possible there could be dual-infections. However, there is a chance that no ransomware will be identified. Some ransomware show few, or very complicated signs, and cannot be determined simply from the ransom note and encrypted sample.
A current list of ransomware that is supported and is displayed on the front page, with the newest additions in bold (all will be bold at launch here naturally).
When the ransomware(s) has been identified, a clean-cut answer will be displayed. You will know the current status of decrypting the data, along with a link to more information on the particular ransomware.
Conclusion
Do not pay the ransom. It only encourages and funds these attackers. Paying the ransom is no guarantee that the ransomware creators will give you access to your data.
When dealing with ransomware:
- You need to decrypt your files
- Use your backups
- Pay the ransomware,
- or lose your data.
Turning on Ransomware Protection for Windows is very easy to do. You can set Ransomware Protection on a single Windows computer. Or, you can write a Group Policy Object (GPO) to turn on this feature. The GPO can set 1000s of computers for Ransomware Protection in seconds.
It is critical to educate your clients on just how serious the ransomware problem is. You need to solidify the importance of being vigilant on any/all aspects of Ransomware Protection for Windows.
Do you Disce? iDisce!
About the Author:
Charles Duncan is a Veteran IT Consultant with a Bachelor of Science Charles Duncan is a Veteran IT Consultant with a Bachelor of Science Degree with Specialised Honours in Computer Science. Excellent experience from founding Crown Computing Incorporated and managing Micro Services for York University. Extensive experience with Linux, Apple, and Windows Operating Systems, and “hands-on” Hardware, and Networking experience. Charles is Microsoft (MCSE), Azure, and Cisco (CCNA) certified. Connect with Charles on LinkedIn and Facebook.
